
Due to the increasing pressures from external and internal threats, organizations are facing challenges that bring them to the forefront of risk and how risk is mitigated, transferred, avoided and accepted. Like financial or reputational risk, cybersecurity risk affects a company’s bottom line. It can drive up costs and impact revenue. It can harm an organization’s ability to innovate and to gain and maintain customers.
Cybersecurity legislation is becoming more profound with at least 42 states having introduced more than 240 bills or resolutions related to cybersecurity and at least 27 states have enacted legislation in 2017. Healthcare, Financial Services, Education, Retail and Government being the hardest hit sectors so far in 2017, it is no wonder that worldwide spending on cybersecurity continues to grow each year.
Small and midsized businesses (SMBs) are driving this growth as they are becoming increasingly aware of security threats. The United States accounted for 61.4% of all breaches in the first half of 2017 and these 10 states accounted for 50% of those; California, Texas, Florida, New York, Pennsylvania, Virginia, Ohio, Illinois, Maryland and North Carolina.
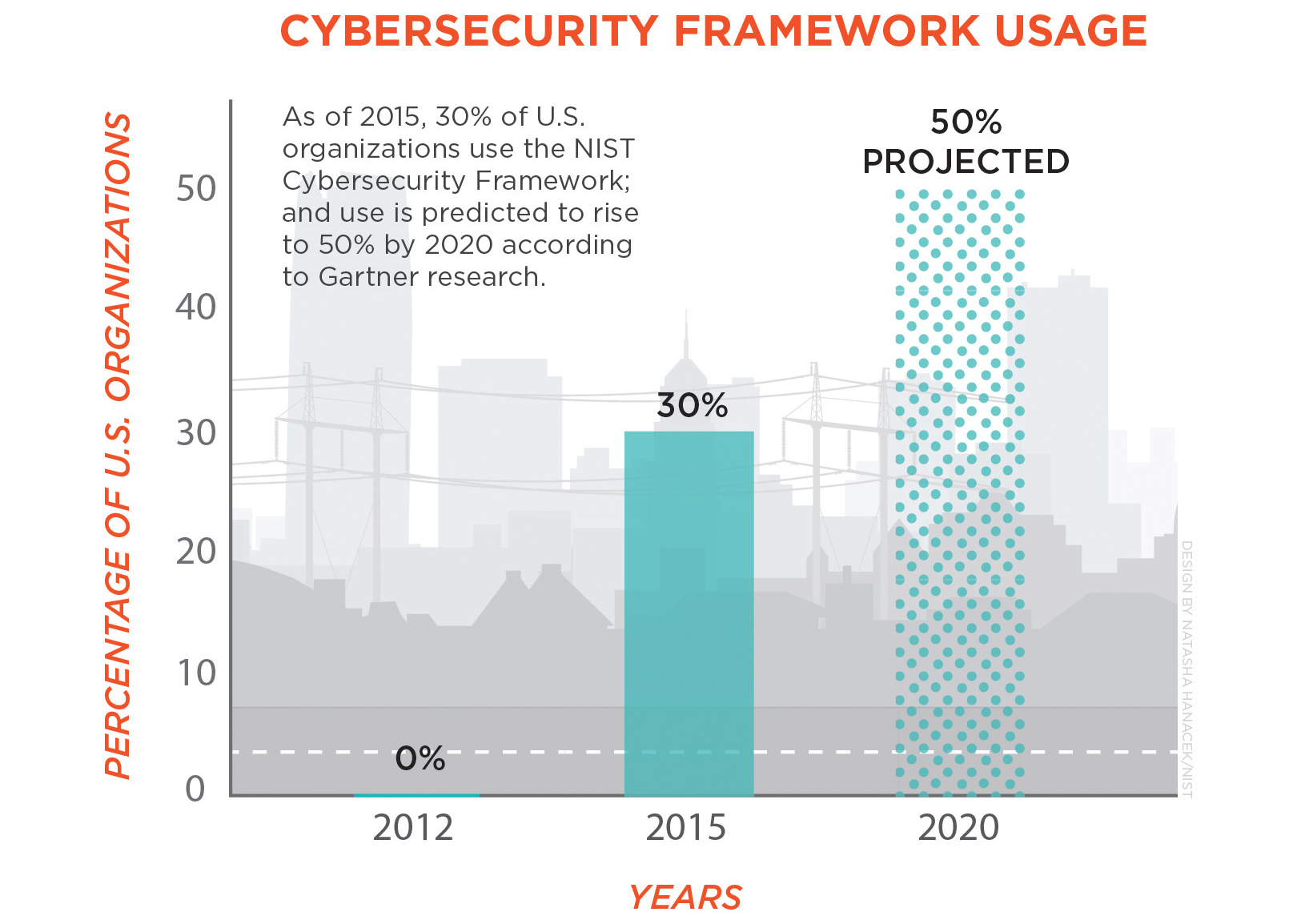
By 2020, it is projected that 50% of US organizations, regardless of size or threat exposure will be adopting the NIST framework for a risk based approach to cyber security. Since there will be such a huge adoption of this over the years, we think it would be a good idea to go through and provide an overview and highlight some of the important aspects.
The NIST Cybersecurity Framework is a set of industry standards and best practices to help organizations and scale across borders to deal with the global nature of cybersecurity threats. It provides a prioritized, flexible, repeatable, performance-based and cost-effective approach to manage cyber security risk. From the Executive level to Operations, It can be used to manage cybersecurity risk across entire organizations or it can be focused on the delivery of critical services within an organization.
Organizations that use, collect, process, maintain, or disclosure protected health information (ePHI) are very high-profile targets for attacks. Within the Framework there is a methodology to protect the privacy and civil liberties of individuals. The methodology was designed to provide guidance to facilitate privacy risk management consistent with an organization’s approach to cybersecurity risk management. By integrating privacy and cybersecurity together, organizations can benefit by increasing customer confidence and enabling more standardized sharing of information.
The Framework provides a common language for understanding, managing, and expressing cybersecurity risk both internally and externally. It can be used to help identify and prioritize actions for reducing cybersecurity risk, and it is a tool for aligning policy, business, and technological approaches to managing that risk.
The Framework consists of three parts:
Framework Core: A set of cybersecurity activities, outcomes, and informative references that are common across critical infrastructure sectors, providing the detailed guidance for developing individual organizational Profiles.
These are broken up into functions and categories, which include:
| Function | Category |
| Identify | Asset Management; Business Environment; Governance; Risk Assessment; and Risk Management Strategy |
| Protect | Access Control; Awareness and Training; Data Security; Information Protection Processes and Procedures; Maintenance; and Protective Technology |
| Detect | Anomalies and Events; Security Continuous Monitoring; and Detection Processes |
| Respond | Response Planning; Communications; Analysis; Mitigation; and Improvements |
| Recover | Recovery Planning; Improvements; and Communications. |
Framework Profile: The Framework will help the organization align its cybersecurity activities with its business requirements, risk tolerances, and resources. The organization can then take steps to close the gaps between its current profile and its target profile.
The Profile is broken up into Tiers:
- Partial
- Risk Informed
- Repeatable
- Adaptive
They describe an increasing degree of rigor and sophistication in cybersecurity risk management practices and the extent to which cybersecurity risk management is informed by business needs and is integrated into an organization’s overall risk management practices.
Framework Implementation Tiers: Provide a mechanism for organizations to view and understand the characteristics of their approach to managing cybersecurity risk. A Profile enables organizations to establish a roadmap for reducing cybersecurity risk.
To read more about this you can refer to the NIST website and download the Cybersecurity Framework document
Building on these standards, guidelines and practices, an organization will be able to:
- Describe their current cybersecurity posture
- Describe their target state for cybersecurity
- Identify and prioritize opportunities for improvement within the context of a continuous and repeatable process
- Assess progress toward the target state
- Communicate among internal and external stakeholders about cybersecurity risk.
It not a replacement for an organization’s risk management process and cybersecurity program. Organizations can use their current processes and leverage the Framework to identify opportunities to strengthen and communicate its management of cybersecurity risk while aligning with industry practices. Alternatively, an organization without an existing cybersecurity program can use the Framework as a reference to establish one.
Risk Management and the Cybersecurity Framework
Risk management is the ongoing process of identifying, assessing, and responding to risk. To manage risk, organizations should understand the likelihood that an event will occur and the resulting impact.
With this information, organizations can determine the acceptable level of risk for delivery of services and can express this as their risk tolerance. With an understanding of their risk tolerance, organizations can prioritize cybersecurity activities, enabling them to make informed decisions about cybersecurity expenditures.
The Framework uses risk management processes (ex. ISO, NIST 800-39, RMP) to enable organizations to inform and prioritize decisions regarding their cybersecurity. It supports recurring risk assessments and validation of business drivers to help organizations select target states for cybersecurity activities that reflect desired outcomes. This will give organizations the ability to improve cybersecurity risk management for IT and other departments.
While every organization will continue to have their own unique risks along with different threats, vulnerabilities and risk tolerances. The Framework provides organizations a structure for cybersecurity by assembling standards, guidelines, and practices that are working effectively in industry today.
Ultimately, it is aimed at reducing and better managing cybersecurity risks.
How much Risk can your organization or your clients afford to take?
At ChannelSOC, we help identify security gaps and deliver actionable recommendations to improve network security, using the latest technology and industry best practices. Achieving and maintaining the right security level for your organization is the core of our services.
Find out more information on our site or email us at: [email protected]

