Vulnerability assessments are a necessary tactical approach to mitigating risk and securing all systems in your environment
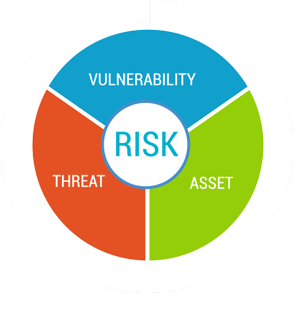
The objective of this analysis is to identify potential security vulnerabilities within specified IP’s, identify threats to those assets, estimate the level or risks and identify options for remediation.
ChannelSOC provides a programmatic approach for evaluating technical, administrative and management security controls across your environment. We conduct tests against your external perimeter and internal systems using real world attacks techniques, both automated and manual.
Identify your security weaknesses, to eliminate the vulnerabilities before unauthorized users can exploit them
Key aspects of a vulnerability assessment
- Methodology development
- Analysis of remediation process and solution development
- Metrics development and reporting
- Manual and automated testing procedures
- Review of network, operating system, application and end-point security measures
- Development of key remediation recommendations
- Policy development to maintain proper vulnerability remediation procedures
Internal and External Vulnerability Scanning
External Vulnerability Scan
This vulnerability scan will utilize hardware outside of your network, to scan your external public facing services for vulnerabilities. We are generally testing for public facing servers, open ports on firewalls and web applications.
Internal Vulnerability Scan
An internal scan will leverage supporting hardware within your environment, that searches for vulnerabilities inside your network. These are generally performed on critical assets, including servers.
Monthly, quarterly or annual vulnerability scanning is available to help develop and manage your vulnerability management program
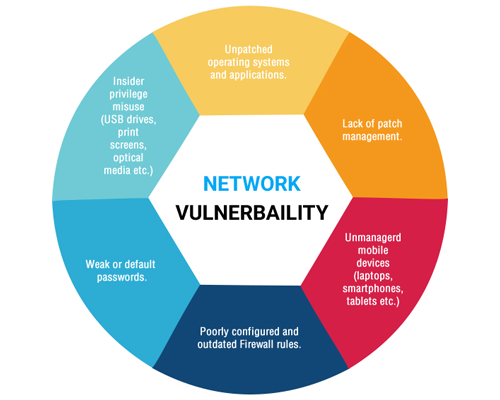
Once vulnerability assessment is completed, we will attempt to validate the vulnerabilities and provide detailed recommendations to fix the problems.
We review your policies and procedures around vulnerability management and provide practical steps to ensure management of vulnerabilities in the future.

